How RFID Works?
Introduction
Long lines at the grocery store - one of the biggest complaints of those who visit the store. Soon, these queues may disappear when the universal product barcode (UPC) will be replaced by smart tags, also called radio frequency ide ntification (RFID) tags. RFID tags are smart barcodes that can interoperate with a networked system to keep track of each product you put in your grocery cart.
ntification (RFID) tags. RFID tags are smart barcodes that can interoperate with a networked system to keep track of each product you put in your grocery cart.
Imagine you go to the grocery store, fill your cart and go right off the door. You no longer have to wait because the cashier punches every purchase from your cart one at a time. Instead, RFID tags will be read by electronic readers that detect every purchase in the cart and punch every purchase immediately. The reader will be connected to a large network that will send information about your products to the manufacturers of the products and the retailer. Your bank will be notified and the check amount will be withdrawn from your account. No queues, no waiting.
RFID Tag
RFID tags, once used only to track cattle movements, are now monitoring consumer products worldwide. Many manufacturers use RFID tags to track the movement of every product they make from the time they are manufactured and until it is taken from the shelf and is thrown into a shopping cart.
Outside the retail industry, RFID tags monitor transport, airline passengers, Alzheimer's patients and pets. Soon, they may even watch your preference for short or creamy peanut butter. Some critics say that RFID technology is becoming too much of our lives — that is, we may not even be aware of all the parts of our lives that this technology affects.
In this article, you will learn about the types of RFID tags, and how these tags can be traced through the entire supply chain. We also look at the non-commercial use of RFID tags and how state departments and the state security system use them.
Re-inventing barcode
Almost everything you buy at retail has a barcode printed on it. These bar codes help manufacturers and retailers track products. They also provide valuable information on the quantity of products purchased and, to some extent, by whom these products were purchased. These codes serve as fingerprints of products made from machine-readable parallel lines that store binary code.
Barcodes such as this one on sparkling water can be found on almost everything we buy.
Created in the early 1970s, to speed up cash register technology, bar codes have several drawbacks:
- To keep track of products, companies must scan each barcode on each box of a single product.
Passing a queue at a check-out point requires scanning each bar code on each item.
The barcode is read-only and cannot send information.
RFID tags are better than bar codes because tags have the ability to read and write. The data recorded on the RFID tags can be changed, updated and blocked. Some stores that have started using RFID tags have found that technology offers the best way to keep track of products for supply and marketing purposes. Through RFID tags, stores can see how quickly products leave the shelves, and who buys them.
In addition to retailing, RFID tags were also used in transportation as tickets for public transport and the subway. Because of their ability to effectively store data, RFID tags can analyze the cost of a trip at a rate and deduct the cost of a trip from the amount that the user puts on the account. Instead of waiting to pay the fare in the ticket booth or throwing coins into the machine, passengers use travel cards with RFID chips as debit cards.
But would you assign your RFID tag to your medical history? Or your home address or the safety of your child? Let's look at two types of RFID tags, and how they memorize and transmit data before we move from grocery shopping to the issue of human life.
Bar Code History
At 8:01, June 26, 1974, a customer at the Marsh supermarket in Troy, Ohio, made the first product purchase with a bar code, a pack of 10 Wrigley's Juicy Fruit chewing gums. This launched a new era in retail sales, which accelerated the queues in front of the cashier and gave companies a more efficient method of inventory control. That chewing gum packaging took place in American history and is currently on display at the Smithsonian National Museum of American History. That historical purchase was the culmination of almost 30 years of research and development. The first system for automatic product coding was patented by Bernard Silver and Norman Woodland, two graduate students from the Drexel Institute of Technology (now Drexel University). They used a pattern of ink that glowed under ultraviolet radiation. This system was too expensive, and the ink was not very stable. The system we use today was introduced by IBM in 1973 and uses readers designed by NCR.
Past and Present of RFID Tags
RFID technology has been developed since 1970, but until recently it was too expensive to use on a large scale. Initially, RFID tags were used to keep track of large items, such as cows, train cars, and baggage on airlines, which were sent over long distances. These first tags, called inductively coupled RFID tags, were complex systems of metal inductors, antennas, and glass.
Inductively coupled RFID tags were powered by a magnetic field generated by an RFID reader. An electric current has an electrical component and a magnetic component — it is electromagnetic. Because of this, you can create a magnetic field with electricity, and you can create an electric current with a magnetic field. The name, "inductively coupled," comes from the essence of this process - the magnetic field induces a current in the wire.
This Texas Instuments RFID tag was manufactured in 1999 and was used to track baggage.
Capacitive-related tags were created later in an attempt to lower the cost of technology. They were designed as disposable tags that could be applied to less expensive items and made as versatile as barcodes. Capacitive-coupled tags used conductive carbon ink instead of metallic inductors for data transmission. Ink was printed on paper tags and scanned by readers. Tags BiStatix Motorola firms were leaders in this technology. They used a silicon chip, which was only 3mm wide, and stored 96 bits of information. This technology did not win popularity with retailers, and BiStatix was closed in 2001 [Source: RFID Magazine].
New developments in RFID include active, semi-active, and passive RFID tags. These tags can save up to 2 kilobytes of data and consist of a microchip, an antenna, and, in the case of an active and a tag of a semi-passive tag, a battery. Tag components are placed in a plastic, silicon or sometimes glass case.
At the main level, each tag works as follows:
Data stored in the microchip chip of an RFID tag is awaiting readout.
The tag antenna receives electromagnetic energy from an RFID reader antenna.
Using power from the internal battery or energy from the electromagnetic field of the reader, the tag sends radio waves back to the reader.
The reader takes radio waves from the tag and interprets frequencies as meaningful data.
Inductively related and capacitively-related RFID tags are not used today because they are expensive and large. In the next section, we will learn more about active, semi-passive, and passive RFID tags.
Active, semi-passive and passive RFID tags
Active, semi-passive and passive RFID tags make RFID technology more accessible and visible in our world. These tags are less expensive to produce, and they can be made small enough to fit on almost any product.
Active and semi-passive RFID tags use internal batteries to power their circuits. The active tag also uses its battery to transmit radio waves to the reader, while the semi-passive tag relies on the reader to supply it with power for data transmission. Since these tags contain more hardware than passive RFID tags, they are more expensive. Active and semi-passive tags are reserved for expensive items that are read at a great distance - they transmit high frequencies from 850 to 950 MHz, which can be read at a distance of 30 meters or more. If you need to read tags at farther distances, additional batteries, I can increase the range of the tag to more than 100 meters [Source: RFID Journal].
Passive RFID tags rely entirely on the reader as a power source. These tags are read at a distance of 6 meters, and they are cheaper to produce, which means that they can be applied to less expensive items. These tags are produced to be disposable, along with disposable consumer goods in which they are placed. Thus, the railcar will have an active RFID tag, and the shampoo bottle will have a passive tag.
Another factor that influences the cost of RFID tags is the ability to save data. There are three types of data storage options: read-write, read-only, and ZMCH (write-once, read-multiple). In the tags for reading and writing data can be added to or written over. In read-only tags, data cannot be added to or written over - it only contains data that is stored in them when they were made. For OMZCH tags, the information may contain additional data (such as a serial number), written once, but they cannot be overwritten.
RFID tag

This tiny RFID tag will be placed on a bottle of moisturizer.
Most passive RFID tags cost between 7 and 20 cents per unit [source: RFID Journal]. Active and semi-passive tags are more expensive, and manufacturers of RFID, as a rule, do not indicate the prices of these tags without determining their range, memory type and quantity. The purpose of the RFID industry is to reduce the cost of passive RFID tags to 5 cents each, as soon as sellers accept them.
In the next section, we will learn how this technology could be used to create a global system of RFID tags with an Internet connection.
Talking tags
When the RFID industry is able to lower the tag price, it will lead to a ubiquitous network of smart packages that follow every stage of the supply chain. Store shelves will be full of cleverly tagged products that can be traced from purchase to the trash can. The shelves themselves communicate wirelessly with the network. Tags will be just one node of this large network monitoring product.
The other two parts of this network are reading devices that communicate with tags and with the Internet, which will provide the connecting links of the network.
Let's look at the real scenario of this system:
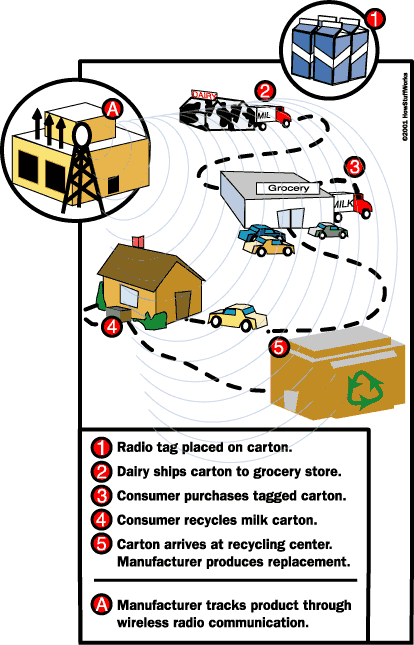
At the grocery store you buy a bag of milk. Milk containers will have an RFID tag that remembers the expiration date of the milk and the price. When you remove milk from a shelf, a shelf can display a specific date of expiration of the milk, or information can be sent via a wireless network to your mobile computer or cell phone.
As soon as you exit the store, you pass through the door with a built-in tag reader. This reader counts the cost of all items in your shopping cart and sends a bill from the groceries to your bank, which is the amount of your bill. Product manufacturers know that you bought their product, and store computers know exactly how much of each product needs to be ordered.
As soon as you return home, you put your milk in the refrigerator, which is also equipped with a tag reader. This smart refrigerator is able to keep track of all the groceries that are stored in it. He can keep track of the products you use, how often you replenish your refrigerator and can tell you when milk or other products go bad.
Products are also traced when they are thrown into a trash can or trash can. At this point, your refrigerator might add milk to your shopping list, or you could program the refrigerator to order these items automatically.
Based on the products you buy, your grocery store will recognize your unique preferences. Instead of receiving universal newsletters with weekly offers of goods in the store, you could get exactly the list that is created only for you. If you have two schoolchildren and a puppy, your grocery store can use customer-focused marketing, and send you coupons for goods such as juice packs and dog food.
For the operation of this system, each product will be given a unique product number. The MIT Automatic Identification Center is working on an Electronic Product Code (RPC), which could replace a bar code. Each smart tag can contain 96 bits of information, including the manufacturer of the product, the name of the product, and a 40-bit serial number. Using this system, a smart tag would communicate with a network called the Object Naming System. This database would receive product data directly from the manufacturer’s computer.
The information stored on smart tags would be written in product markup language (PML), which is based on Extensible Markup Language (XML). PML would allow all computers to communicate with any computer system, just as Web servers read Hypertext Markup Language (HTML), the common language used to create Web pages.
We haven't got it yet, but RFID tags are more meaningful in your life than you can imagine. Wal-Mart and Best Buy are just the two main sellers that use RFID tags for supply and marketing.
Some critics believe the disturbing idea of traders tracking and recording purchases. But retail is not the only industry using RFID technology. In the next section, we will learn how the government uses RFID tags.
RFID issued by the government

While many consumers happily — or indifferently — buy goods tagged with RFID tags, some people in the government believe that passports must be with embedded RFID chips.
On August 14, 2006, the State Department began issuing electronic passports, or e-passports. Concerned about the terrorist attacks of September 11, 2001, the Department of Homeland Security (DHS) proposed an e-passport as a safety measure for air travel security, border crossing security and more efficient customs control at airports. The enhanced security features of the e-passport — the identification number of the chip, the digital signature, and a photo that acts as a biometric identifier — make up a passport that cannot be faked.
An e-passport will help improve security, but with so much personal information embedded in the document, many questions arise about the possibility of identity theft. Two possible types of identity theft that could occur with e-passports:
Downloading happens when someone uses an RFID reader to scan data from an RFID chip without the knowledge of the owner of the e-passport.
Eavesdropping happens when someone reads frequencies emitted from an RFID chip when read by an official reader.
However, DHS insists that the e-passport is perfectly safe to use, and that proper precautions have been taken to ensure user privacy.
To protect against downloading, the e-passport contains a metal screen. This screen is set between the cover of the passport and the first page. When an e-passport is closed, it cannot be read at all, when it is open, it can only be read by a scanning device that is less than 10 centimeters away [source: Department of State].
To guard against eavesdropping, DHS found that all areas where the e-passport is revealed must be completely covered and placed on the screen so that the signals cannot be read by an unauthorized RFID reader.
The Australian passport served as a model for the new United States e-passport.
E-passport costs 97 dollars. While the cost may seem high to you, the cost of installing RFID readers at airports is even higher. The adoption of an e-passport will require gradual changes, but authorized people are already discussing what total protection and improved biometrics the next generation of e-passports will have.
The debate over e-passports pales in comparison to debates over human chipping. Next, we'll learn what RFID microchips are doing in living things.
Real ID
From air traffic to road transport, security poses great problems, and some people feel that they are being watched more closely than ever before. The real ID is a program developed by the 9/11 Commission. It is intended to improve the way official identification is issued. While the Real ID is waiting for approval (and hotly debated), the first proposed Real ID is Real Driving License. DHS issued a note on the Rules for Real Driving License on March 1, 2007. A real driver's license can be extended to provide you with an easy border crossing in Canada, and more standard driver's licenses, it also gives you access to federal agencies, the federal airport and nuclear power plants [source: Department of State Security]. States will choose to implement RFID in Real Drivers License, instead of the current two-dimensional barcode current.

